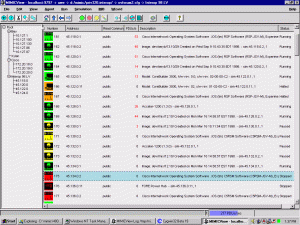
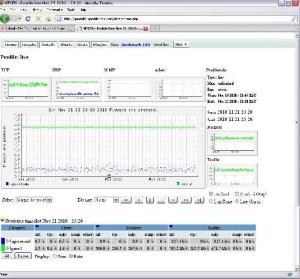
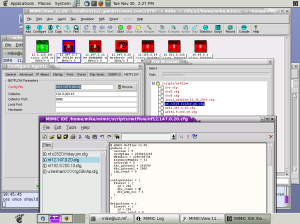
Server monitoring is essential to important IT infrastructural continuance. A great monitoring system not just creates alarm in reaction to important events but also offers the analytical tools to work on the bigger scenario in IT industry. For server monitoring purposes, some typical protocols are employed in the IT industry. However, SNMP is by far the most common choice and extensively used podium for server monitoring.
SNMP – a brief introduction:
Simple Network Management Protocol, SNMP is a standard protocol used to monitor servers on IP network. However, the use of SNMP extends to other devices comprising printers, switches, routers, etc. This protocol has a widespread use in NMS (Network Management System). SNMP checks each of the network-affixed devices for conditions worth assuring attention from the manager.
Working process of SNMP:
On the managed system, which organizes the system configuration – the management data are represented in the form of variables. As soon as the system is discovered by a management application, it collects all the configuration data. i It may change the configurations sometimes as needed. In case of normal SNMP uses, the administrator has a horde of tools on the management computer to perform all these operations. Around-the-clock, of the SNMP agent on the managed systems communicates with the management system. This agent takes the accountability of sending crucial information to the administrator via SNMP.
Why employ SNMP to monitor server?
SNMP is the best choice as far as server monitoring is concerned. SNMP sends easy-to-understand info to the network managers. That information helps in proper management of several devices. Only a single interface is adequate for the purpose of device administration through SNMP. It is an efficient and best device management system that makes sure a good communication between the management station and agents from various vendors. 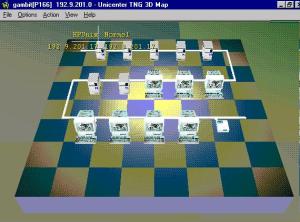 The complete network analyzer – a crucial tool of server monitoring through SNMP – provides timely analysis. Also, the analyzer is allocated the responsibility of viewing and handling statistics from the SNMP compliant tools. With the help of some crucial tools, SNMP does various important tasks comprising network interface mapping. An all-inclusive and extensive checking exemplifies the SNMP server monitoring. Regular monitoring and status display of diferent devices is a guarantee that you avail the best for your server administration and its smooth operation.
The complete network analyzer – a crucial tool of server monitoring through SNMP – provides timely analysis. Also, the analyzer is allocated the responsibility of viewing and handling statistics from the SNMP compliant tools. With the help of some crucial tools, SNMP does various important tasks comprising network interface mapping. An all-inclusive and extensive checking exemplifies the SNMP server monitoring. Regular monitoring and status display of diferent devices is a guarantee that you avail the best for your server administration and its smooth operation.
 The complete network analyzer – a crucial tool of server monitoring through SNMP – provides timely analysis. Also, the analyzer is allocated the responsibility of viewing and handling statistics from the SNMP compliant tools. With the help of some crucial tools, SNMP does various important tasks comprising network interface mapping. An all-inclusive and extensive checking exemplifies the SNMP server monitoring. Regular monitoring and status display of diferent devices is a guarantee that you avail the best for your server administration and its smooth operation.
The complete network analyzer – a crucial tool of server monitoring through SNMP – provides timely analysis. Also, the analyzer is allocated the responsibility of viewing and handling statistics from the SNMP compliant tools. With the help of some crucial tools, SNMP does various important tasks comprising network interface mapping. An all-inclusive and extensive checking exemplifies the SNMP server monitoring. Regular monitoring and status display of diferent devices is a guarantee that you avail the best for your server administration and its smooth operation.
Server monitoring through SNMP uses the different network management devices to get the best piece of info concerning the network blockage. As the whole monitoring system is based on performance details from the devices, one can always anticipate SNMP to work wonderfully toward server monitoring.