SNMP (Simple Network Management) simulator software is intended for testing SNMP managers against a huge number of SNMP agents that depict a potentially extremely large network colonized with different types of SNMP-competent devices.
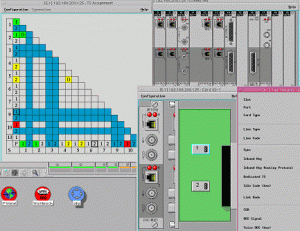
General use for SNMP simulator software begins with either ready devices provided with the simulator or recording the test lab or production network. Another alternative is to create a simulation from MIB files. This is a good option if you don’t access to a device. Once you’ve your recording available, Simulator could use it to create a device that responds to SNMP queries just like a real SNMP agents on the recorded device.
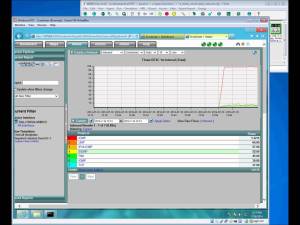
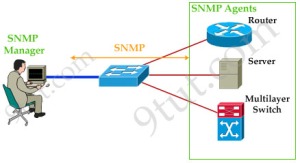
 SNMP based management applications can talk to the Simulator using SNMPv1, SNMPv2c or SNMPv3. For SNMPv3 it needs SNMP context name in queries, whereas for SNMPv1 it needs a particular SNMP community name to access the managed objects.
SNMP based management applications can talk to the Simulator using SNMPv1, SNMPv2c or SNMPv3. For SNMPv3 it needs SNMP context name in queries, whereas for SNMPv1 it needs a particular SNMP community name to access the managed objects.
It’s also feasible with the SNMP simulator software to send different type of responses to network management application’s address, not just SNMPv3 context names.
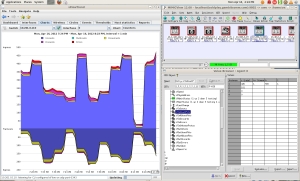
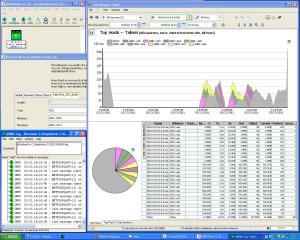
MIMIC SNMP Agent Simulator creates a network of up to 100,000 SNMP manageable devices. MIMIC simulated devices respond to SNMPv1, SNMPv2C and SNMPv3 queries. Now you can easily create any SNMP based device with any number of public or private MIBs to run a large variety of device configurations with your SNMP management application. It includes large device, network and MIB libraries, along with many ready scripts to create variety of scenarios. It is easy to create disastrous conditions like black out, network segment down, core router down etc.