The general idea behind the network simulation of applications and network services is to check whether they can meet your particular requirement. When you have a network application or server to use in complex manner for real-life situations, you need to make sure that the servers you use are deprived of any faults. So to avoid this problem and get the desired level of performance, Network Simulation will work as best software. There are some special features of this simulation software and it has been highlighted here.

. Perfect Simulated Applications-
Web applications need to perform as per the expectation of the maker. If you have a web-based application which has certain faults and is unable to meet your criteria, you can fail to meet your targeted expectations. Network simulator or web simulator helps you to avoid this through its featured advantage. You can use the services to assess your software performance and its response to specific input time.
. Application Based Special Features-
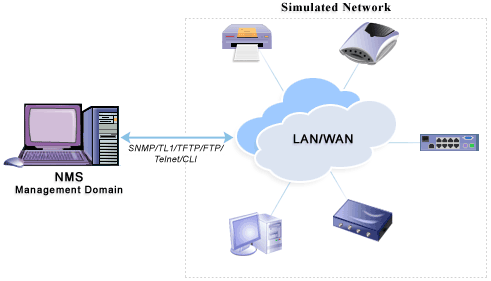
It is necessary to assess the performance of a server related to different application types. Since every application exists and come with different feature, so as per the vital use of simulation software you need specific application. For eg. Network Management application simulation requires the simulation to connect within the multiple SNMP and NetFlow based devices and application.These servers need to function properly if the application is meant to work with mail. On other hand, Webclient come up with long list to stimulate the HTTP, HTTPs, XML, SOAP and REST servers.
. Easier Setup-
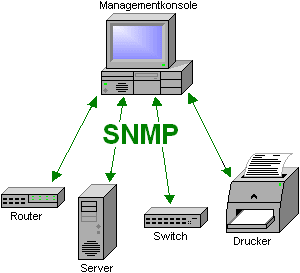
You might end up coming to simulation software that are not easy to set up. As you spend hours trying to set your system causing much time consuming and even laborious. The best way to avoid such issues is to look for software that is easy to setup and has many ready simulations, eg. Ready SNMP and NetFlow based Cisco, Juniper etc devices. This will help you lot way to achieve desired result and without having to face any problem.
Meet Your Current & Future Test Development Target with Agent Simulator

Now when you are developing an application, you can do is to test your product with real-life situation. Agent simulator can help you will all possible featured test cases that you can think about. This again can let you root out all inconsistencies and possible flaws in performance.
A virtual agent simulator should be one that works in flexible environment with various scenarios and can be used by both professionals and beginners to render desired solution. Here the beginners will get a good understanding to the complexity while professional can develop better skills and sort problems that arise out of networks.
































 Two-factor verification is another confirmation improvement, which requires the use of two validation factors: a learning factor together with an ownership factor or an inherence factor.
Two-factor verification is another confirmation improvement, which requires the use of two validation factors: a learning factor together with an ownership factor or an inherence factor.

















