NetFlow was first introduced on Cisco routers that offer the capability to collect IP network as it gets into or exits an interface. By checking the data supplied by NetFlow, a network manager can decide things like the source & destination of traffic, class of service, and also the cause of blocking. A usual flow monitoring setup consists of three major components:
 • Flow exporter – Aggregates packets into flows and exports flow records towards one or more flow collectors.
• Flow exporter – Aggregates packets into flows and exports flow records towards one or more flow collectors.
• Flow collector – Accountable for response, storage & pre-processing of flow data obtained from a flow exporter.
• Analysis application – Verifies received flow data in the context of infringement detection or traffic profiling.
Protocol description:
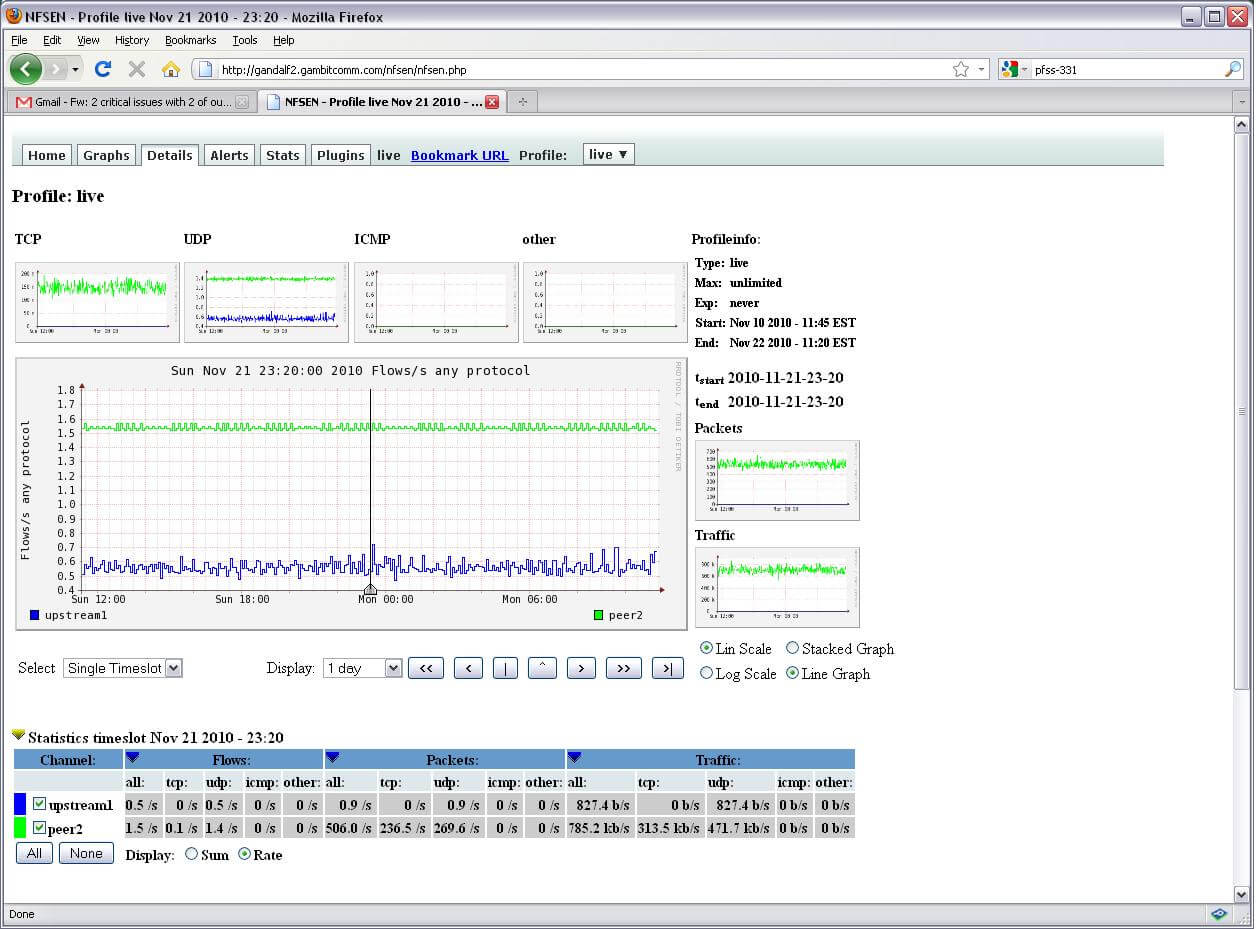
Switches and routers that support NetFlow, can pull together IP traffic data on entire interfaces where NetFlow is allowed and later export those data as NetFlow records towards a minimum of one NetFlow collector.
Network flows:
A network flow can be described in several ways. Cisco standard NetFlow edition 5 describes a flow as a unidirectional succession of packets that all share the following seven rules:
 • Source IP address
• Source IP address
• Ingress interface
• IP protocol
• Destination IP address
• Source port for TCP or UDP
• Destination port for TCP or UDP, type & code for ICMP or other protocols
• IP Type of Services
Netflow interfaces:
Usually, NetFlow is allowed on a per-interface basis to limit stack on the router mechanism involved in NetFlow, or to limit the quantity of NetFlow records exported.
Also, some NetFlow implementations permit the surveillance of packets on the egress IP interface, but this should be employed with care.






0 comments:
Post a Comment